G-Suite End-Users Hardened Against Phishing Attacks with BIMI
Google is implementing the BIMI standard to help protect G-Suite users from spam and fraud, and to help filter phishing attacks.
Phishing attacks are emails that attempt to trick the user to click on a hyperlink to access a system they shouldn’t. In order to convince the user to click, hackers will often include the business logos of trusted brands to bestow a feeling of legitimacy and importance.
On July 21, 2020, Google announced a new security feature that’ll be rolled-out to G-Suite users to help protect them from these kinds of attacks.
The feature implements an emergent email standard called Brand Indicators for Message Identification (BIMI) and its function is to uniquely verify the use of corporate logos using the DMARC system - the same system that’s used to validate the authenticity of an email sender.
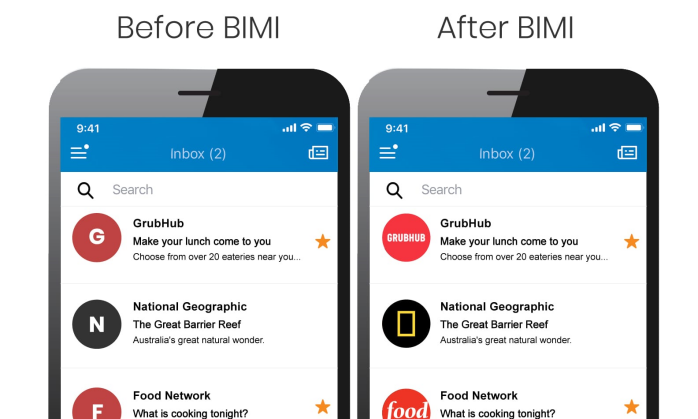
Emails delivered to Google’s mail system are scanned for fraud and abuse. Under BIMI, a registered brand logo will be validated and presented to the G-Suite end user in the round avatar slot aside an email. It’s a visual cue that both re-affirms brand-trust and indicates safety to the end user.
Messages that fail validation for the use of a corporate logo are filtered from the end user.
The technical side of BIMI requires email senders to:
use SPF and DKIM, and to publish a specific DMARK enforcement policy for the domain of either “p=quarantine” or “p=reject”.
register their logo with the BIMI working group and publish a BIMI record;
acquire a Verified Mark Certificate for their logo (a Google-specific requirement currently offered by only Entrust, DataCard, and DigiCert).
All of these controls benefit the G-Suite user as fraudulent use of corporate logos would potentially be filtered, making their use within spam and phishing attacks useless.
Google intends to implement this feature (and many others related to mail safety) over the next year.
Microsoft is the Problem, Not the Solution
Microsoft has a proven track record of failure: updates prone to harm systems, vulnerabilities that allow ransomware to exist, unacceptable online compromises and downtime … nobody can trust Microsoft products in their small business.
On Wednesday July 15, 2020 - across the world - millions of Microsoft customers went to open Outlook and it crashed. Completely. Users couldn’t access their email using their Windows computer at all - not unless they bypassed Outlook and went online to use a web-based version of Outlook.
Microsoft eventually posted a server-side fix for the issue, rolling it out around noon PST. This is to say that millions of people - on tax day in the United States, no less - lost nearly a day’s worth of productivity.
And Microsoft just shrugged.
In February 2020, Microsoft released security updates that deleted the private data of Windows users. This came on the heels of over four years of disruptive updates that spoiled industry confidence and forced Microsoft to try and explain themselves; even an ex-Microsoft employee described the quality control problems at Microsoft as being systemic.
And Microsoft just shrugged.
So how about - in January 2019 - when Microsoft Office365 was down for two whole days?
Yeah, Microsoft just shrugged.
Meanwhile, Microsoft’s Office 365 security is equally questionable. In 2020 alone, to date:
January 2020. Hackers use malicious apps to gain access to Office 365.
April 2020. An alert from US-CERT describing the vulnerability of millions of MsO365 users; more than one million compromised accounts per month.
May 2020. A hacking threat to Microsoft Teams was announced, threatening another 75 million users.
Microsoft just shrugged.
And finally, ransomware is a significant issue: attacks by aggressors who extort users by encrypting their data. Yet, Microsoft’s mediocre quality control is responsible for the most prominent malware of 2018-2020:
Cryptolocker. It exploits a vulnerability in the Windows platform.
Wannacry. It exploits a vulnerability in the Windows platform.
Cryptowall. It exploits a vulnerability in the Windows platform.
Locky. It exploits a vulnerability in Microsoft Word.
Petya. It exploits the file system of Windows.
Microsoft just shrugs.
One could ascertain that the problem is that Microsoft doesn’t give a hoot about its customers.
Others might suggest that Microsoft looks at systemic vulnerabilities as a marketing opportunity to convince users to upgrade or replace their computer systems.
Yet others could criticize Microsoft’s shoddy quality control.
Whatever the reason, Microsoft is chiefly responsible for the lack of security, quality, and confidence in their products and services.
It’s Microsoft’s inattention to these matters that put small businesses and their data at risk. Our computing platforms should be ever more resilient, more reliable, and more secure - every year - but Microsoft’s solutions prove the inverse.
It is my opinion that it would behoove any small business to seriously consider in what ways they could minimize the use of Microsoft’s products within their control.
And here’s the great news: there’s a ton of other options for small business that doesn’t involve Microsoft solutions. Ask me how.
Related Links:
2021.03.17. Microsoft Releases Emergency Patches to Allow Users to Print.
2021.03.06. Exchange Server Hack Morphs Into a Global Crisis.
2021.01.14. A Single Icon on your Desktop Can Corrupt Win10’s File System.
2020.12.24. Hackers Accessed Microsoft Cloud Customers Info Through 3rd Party.
2020.12.17. Microsoft 365 Was Hacked; The Government was Compromised.
2020.12.11. New Malware Can Infect 30,000 Windows Machines a Day.
2020.10.21. Windows 10 emergency update: US government just issued warning
2020.10.19. Disastrous Windows 10 update is reportedly breaking some PCs
2020.09.23. Windows Updates Appear to be Broken Again
2020.09.19. Homeland Security Urges Immediate Patching Against ZeroLogon Exploit.
2020.09.17. Microsoft 360 MFA is insecure and has been for years; fix coming in April 2021.
2020.09.05. .NET Used by Malware to Create Excel Docs That Bypass Security Checks.
2020.09.02. Windows Defender Can Be Used to Download Malware.
2020.09.01. New Windows 10 Update Could Leave Users Without an Internet Connection.
2020.08.30. Microsoft Leaves a Windows 10 Active Security Exploit Unfixed for 2 Years.
2020.08.27. Windows 10 Could Kill your SSD.
2020.08.20. Microsoft Makes it Harder to Disable Native AV Software.
2020.08.11. Windows 10 Error is Playing Havoc with User Passwords.
2020.08.07. A Old Microsoft Word Doc and a Zip File Can Hijack a Mac.
2020.08.02. Microsoft Edge is Malware.
2020.07.25. Hackers seizing on trust placed in popular Microsoft Office software.
2020.07.27. Opening and closing your laptop could be enough to crash Windows 10.
2013.07.11. Microsoft collaborated with NSA to allow access to email servers without warrant.
Home Routers are a Huge Risk
Home routers aren’t receiving security updates. Because of that, they’re vulnerable to attack, potentially exposing your data and home to hackers. Hire a computer consultant to help you upgrade your router.
So a little while ago, I wrote about the risks that remote workers face while working from home.
A recent study of home routers does well to illustrate these vulnerabilities.
In a study entitled Home Router Security Report 2020 conducted by FKIE, it was found that 43/127 commercial routers hadn’t received security updates in the last year from the original equipment manufacturer (OEM), despite the fact that these devices are affected by hundreds of known vulnerabilities. In the worst cases, the devices hadn’t bee updated by the OEM in more than five years.
Over ninety percent of the evaluated routers run versions of the Linux operating system. Yet, the updates provided to the routers fall far behind the standards we’d expect for desktop or server machines running the same operating systems. These vendors could distribute security patches and updates several times a year, but often they do not.
FKIE’s study only complements a 2018 study conducted by American Consumer Institute demonstrating that 83-percent of sampled routers were found to have an average of 186 vulnerabilities to potential attacks in the router’s firmware.
Such evidence suggests:
Home router manufacturers aren’t preparing firmware updates in a timely fashion;
Users are not applying available updates in a timely fashion, or, may not understand how.
This is a severe problem, especially in the age of COVID as many millions of workers are conducting important commercial business on the backs of outdated router firmware with known bugs.
But you can do better. Hiring a computer consultant to investigate your router, update its firmware, or replace the router, can secure your small business. It’s a practical step in deterring potential aggressors and in safeguarding your information assets. Just ask us how it’s done.
R