Google Workspace Security Audit
Most Google Workspace environments are deployed with convenience in mind, not security. That means sensitive company data, email, and files may be more exposed than business owners realize. Our Google Workspace Security Audit identifies risks, closes gaps, and hardens your Workspace environment against account compromise, data leakage, and regulatory exposure.
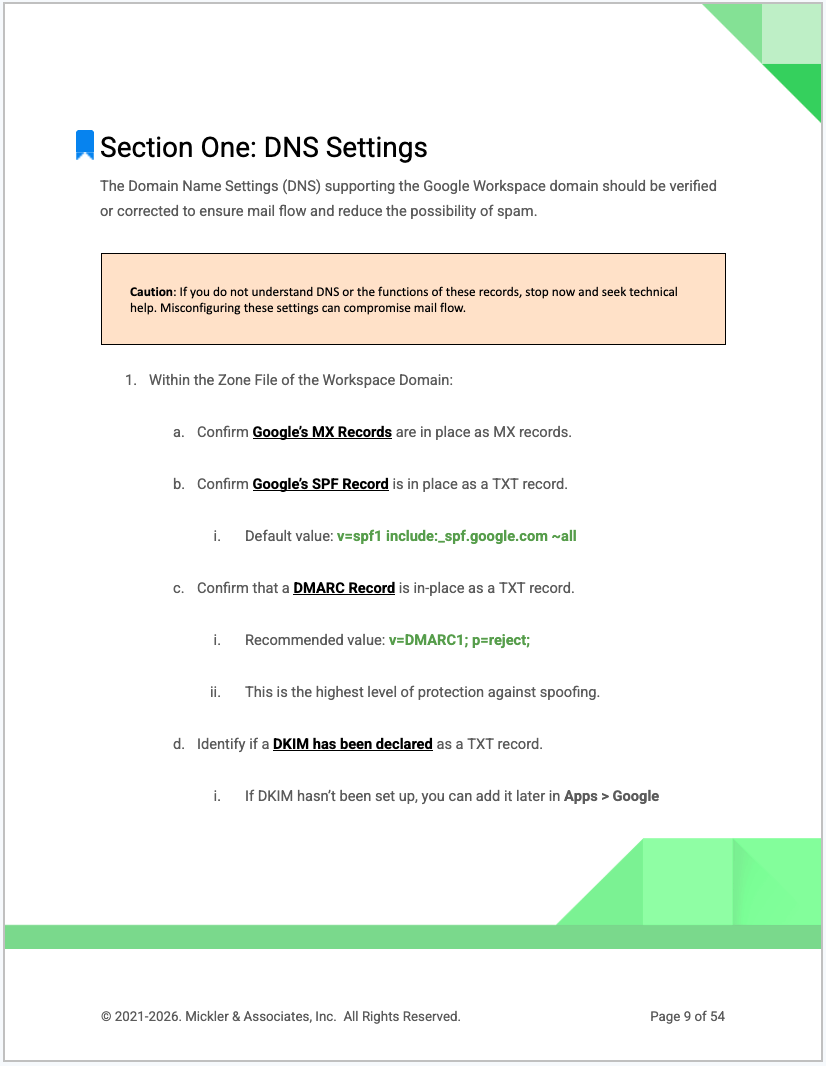
DNS & Mail Authentication Review. Verification of MX, SPF, DKIM, and DMARC records to ensure proper mail flow, domain trust, and anti-spoofing protection.
Super Administrator & Privilege Audit. Review of super admin accounts, delegated roles, privilege creep, alerting, and least-privilege alignment.
User Account & Directory Hygiene. Audit of active users, suspended accounts, shared/role accounts, aliases, licensing, and user lifecycle management.
Authentication & Access Security Controls. Evaluation of password policy, 2FA enforcement, account recovery settings, and session management.
Google Workspace Policy Hardening. Review of core administrative policies, including Less Secure Apps, MDM baseline, session controls, and data export restrictions.
Gmail Security & Anti-Abuse Controls. Assessment of phishing and malware protections, spoofing defenses, forwarding risks, legacy protocol use, and routing rules.
Google Drive & Data Sharing Controls. Analysis of internal and external sharing, public link exposure, Shared Drive ownership, and data leakage risks.
Groups, Sites & Collaboration Surface Review. Evaluation of Google Groups, Sites, Calendar sharing, and Chat settings to reduce unnecessary exposure and external communication risks.
Marketplace & Third-Party App Risk Review. Audit of connected OAuth and Marketplace apps with access to Workspace data and services.
Mobile Device & Endpoint Governance. Verification of Basic MDM policies, device access controls, and protection of Workspace data on mobile endpoints.
Generative AI & Data Exposure Considerations. Review of Gemini/AI access, data handling risks, acceptable use expectations, and service enablement decisions.
Logging, Alerting & Due-Care Controls. Confirmation of audit logging, administrative alerting, and evidence of defensible security practices aligned with due care.
Risk Summary & Hardening Recommendations. Prioritized findings with actionable steps to reduce risk, improve accountability, and strengthen the overall Workspace security posture.